Mobile Device Management System and EMR Security in …
26 hours ago · Patient Portal Outputs. The literature explored some, but not all, potential outputs of patient portal implementations. Most of the studies assessed implementation of patient portals using interim outcomes such as user perceptions, and few studies addressed important objective outcomes such as length of stay, morbidity, or mortality [2,4,20,54]. >> Go To The Portal
How can hospitals improve patient access to their EMR information?
Introduction The increasing adoption of electronic medical records (EMRs) by hospitals presents an opportunity for patients to access their clinical data and actively participate in their care via the EMR. Hospitals and other health care organizations can facilitate patient access to their EMR information through patient portals.
How mobile EHR apps are transforming the healthcare industry?
In mobile EHR apps, incorporating the remote patient monitoring feature helps physicians to collect necessary data from patients’ devices. The patient data can directly reach physicians’ mobile EHR app, which helps them enhance their care service.
Who can benefit from virtual healthcare EMR systems?
Elderly patients and chronic needs can also benefit from virtual healthcare EMR systems. They can have virtual consultations through video calls or chatbots. Medical EMR systems and applications provide health access to patients from the comfort of their homes.
What is the role of EMR in healthcare?
Currently, EMR systems in healthcare are designed to address specific requirements for patients or healthcare providers. EMR solutions are applied toward correspondence, coordination, clinical data analysis, or even pharmacy management. EMR/ EHR systems, in the current space, are focused on specialization and micromanagement.
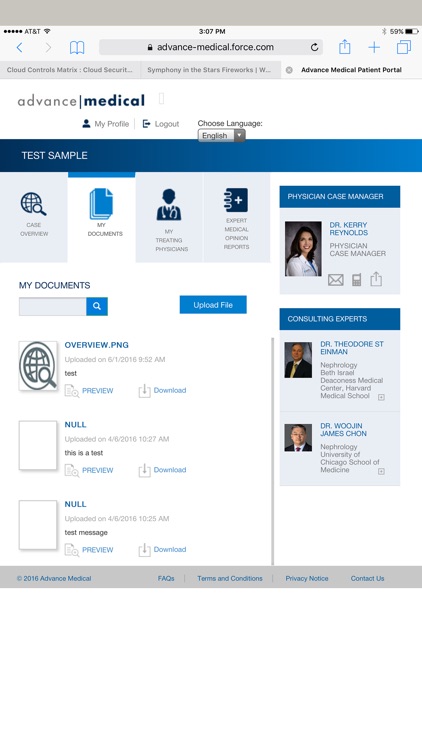
How are patient portals secure?
Patient portals have privacy and security safeguards in place to protect your health information. To make sure that your private health information is safe from unauthorized access, patient portals are hosted on a secure connection and accessed via an encrypted, password-protected logon.
How do you implement a patient portal?
7 Steps to Implement a New Patient Portal SolutionResearch different solutions. ... Look for the right features. ... Get buy-in from key stakeholders. ... Evaluate and enhance existing workflows. ... Develop an onboarding plan. ... Successful go-live. ... Seek out painless portal migration.
What are the three 3 factors that affect EMR?
The interviewees at the hospital identified three main reasons for adopting the system: the need for information within the organization, to integrate information from different systems, and to improve value for end users and patients.
How secure is the EMR?
Generally speaking, EMRs are just as safe, if not safer, than paper forms, and they offer many benefits that make them ideal for use in busy medical offices and hospitals. But that doesn't mean they can't be compromised.
Is a patient portal an EHR?
Electronic health record (EHR) patient portals provide a means by which patients can access their health information, including diagnostic test results. Little is known about portal usage by emergency department (ED) patients.
What are the benefits and challenges of implementing a patient portal?
What are the Top Pros and Cons of Adopting Patient Portals?Pro: Better communication with chronically ill patients.Con: Healthcare data security concerns.Pro: More complete and accurate patient information.Con: Difficult patient buy-in.Pro: Increased patient ownership of their own care.
What are the factors that may hinder the implementation of electronic health record?
The most significant barriers were lack of national information standards and code sets (62 percent), lack of available funding (59 percent), concern about physician (51 percent), and lack of interoperability (50 percent) (8).
What factors can influence the implementation of a health care network?
Healthcare settings included primary care, secondary care and home care. Factors important for implementation were identified at the levels of the following: the individual e-health technology, the outer setting, the inner setting and the individual health professionals as well as the process of implementation.
What factors should you consider when researching electronic health systems?
These five aspects should be carefully examined before choosing software so that the practice is in a good position to achieve its goals.Software design. The most crucial - and obvious - consideration to make is about the software itself. ... Vendor reputation. ... Costs. ... Customization. ... Long-term goals.
How do you protect against EMR?
5 Tips for Protecting Your Electronic Health RecordsPerform Risk Assessments Regularly. Don't underestimate the value in performing routine Risk Assessments. ... Perform Vulnerability Scans & Penetration Tests. ... Utilize Encryption. ... Perform Updates & Patch Your Systems. ... Check Your Audit Logs.
What safeguards can be used to protect a patient's EHR?
A few of the safety measures built in to electronic health record ( EHR ) systems to protect your medical record may include: “Access control” tools like passwords and PIN numbers, to limit access to patient information to authorized individuals, like the patient's doctors or nurses. "Encrypting" stored information.
What 3 security safeguards are used to protect the electronic health record?
The three pillars to securing protected health information outlined by HIPAA are administrative safeguards, physical safeguards, and technical safeguards [4].
Who is the target market for EMR?
Hospitals or enterprises are often the target market of EMR software companies such as Athenahealth, McKesson, Epic, Cerner, eClinicalWorks, Allscripts, NextGen, drChrono, and Meditech, etc. and they usually provide ideal EHR software solutions for larger corporations such as ACOs, PCMH, IPAs, CINs (Clinically Integrated Networks), and Public Health Departments, etc. These EMR software companies usually offer features like integration with multiple other software and medical devices, inventory management modules, interface with local labs (LIS), machines and diagnostic equipment along with drug dispensing (pharmacy management software) and electronic medication administration record (EMAR), etc.
What is EMR refill?
Most of these EMR Systems have an exclusive e-Prescription (e-Rx) module for patients to enter their information and then submit the prescription request. The staff of the provider then verifies this request and takes the next step.
What is EHR software?
The term EMR Software or EHR Software ( Electronic Health Records) is basically used for the electronic documentation and maintenance of medical records for patients via computer or a mobile device. EHR Software essentially improves the efficiency of practice by helping in making more accurate documentation of the encounters resulting in improved profitability. Its usability has been recognized and it became a part of the Health Information Technology for Economic and Clinical Health Act (HITECH) in 2004.
How many EMR companies are there?
With over 600 EMR Software Companies, it is not easy to find the right one. One of our EMR Software experts will call you back and suggest which EMR software will meet your needs!
Why is patient portal important?
The most compelling reason to implement a Patient Portal Electronic Health Records (EHR) Software involves the Health Information Technology for Economic and Clinical Health (HITECH) Act of 2009. This Act offers practices incentive to invest in healthcare IT systems to achieve Meaningful Use (MU) requirements. The final stage of the HITECH Act requires providers to allow patients access to information through a portal for their own use. These tasks can be handled in the most efficient method through a Patient Portal EMR Software.
What is CareCloud EMR?
CareCloud EMR Software is a cloud-based integrated Electronic Health Records (EHR) Software that provides Patient Management (PM) software and Medical Billing services to practices and practitioners , whether it is a small f... read more
Why is it important to have a medical billing system?
Like all other software solutions needed by a medical practice, it is very important for a healthcare organization to have a strong billing system to be able to communicate with insurance companies and to charge all the services rendered. A Medical Billing Software works best when integrated with EMR software. The clinical documentation complies with all the mandatory standards and forms a financial document that is sent electronically to insurance carriers or financiers so that they can validate and process at their end. This helps streamline operations and various administrative tasks and makes sure everyone is on the same page where financial matters are concerned. By using the Medical billing Software system, practices are able to produce patient statements, confirm patient eligibility, and generate claims and much more. Medical billing solutions integrated with EMRs prove to be ideal for healthcare organizations who wish to manage to bill in-house.
How does EMR help patients?
Hospitals and other health care organizations can facilitate patient access to their EMR information through patient portals. Patient portals can provide secure, online access to personal health information [1] such as medication lists, laboratory results, immunizations, allergies, and discharge information [2]. They can also enable patient-provider communication using secure messaging, appointments and payment management, and prescription refill requests [2,3].
How does a patient portal improve patient engagement?
Patient portals may enhance patient engagement by enabling patients to access their electronic medical records (EMRs) and facilitating secure patient-provider communication.
What are the inputs and outputs of a patient portal?
The inputs are the material (eg, hardware and software) and nonmaterial (eg, leadership) components that facilitate or impair the establishment or use of the portal. Processes include the interactions of the users with the portal. Outputs comprise the results of the implementation or the use of the portal. Through the analysis, we identified 14 themes within these three categories, shown in Textbox 1.
How does patient involvement improve quality of care?
Promoting patient involvement in health care delivery may lead to improved quality and safety of care [14,15] by enabling patients to spot and report errors in EMRs, for example [6]. Some patients recognize the role of patient portals in their health care, reporting satisfaction with the ability to communicate with their health care teams and perform tasks such as requesting prescription refills conveniently [3,16]. Portal use may reduce in-person visits, visits to emergency departments, and patient-provider telephone conversations [3,8-10,12,16]. Despite the potential of portals, already used in the ambulatory setting for some time, implementation in the inpatient setting has only recently gathered momentum [17-19]. The inpatient setting presents additional challenges for implementing patient portals [18,20]. Clinical conditions leading to hospitalization are often acute and the amount of medical information generated during this time can be extensive, which may overwhelm patients [20] and challenge information technology to rapidly display this information.
Why are patient portals important?
While the evidence is currently immature, patient portals have demonstrated benefit by enabling the discovery of medical errors, improving adherence to medications, and providing patient-provider communication, etc. High-quality studies are needed to fully understand, improve, and evaluate their impact.
What are barriers in portals?
Barriers: factors that hinder widespread adoption or portal use
What is portal design?
Portal design: umbrella term for all design-related aspects of the portal including portal interface, content, features, and functions
How does a patient portal improve patient engagement?
Patient portals may enhance patient engagement by enabling patients to access their electronic medical records (EMRs) and facilitating secure patient-provider communication.
How do patient portals benefit the patient?
Conclusions: While the evidence is currently immature, patient portals have demonstrated benefit by enabling the discovery of medical errors, improving adherence to medications, and providing patient-provider communication, etc. High-quality studies are needed to fully understand, improve, and evaluate their impact.
Where is the Centre for Health Services Research?
1 Centre for Health Services Research, Faculty of Medicine, The University of Queensland, Woolloongabba, Australia.
What are the risks associated with the testing and implementation of the new EHR system?
The risks associated with the testing and implementation of the new EHR system are those related to not achieving the objectives set for the EHR implementation. Having data that is incomplete, missing or misleading, open or incomplete patient orders, procedures and policies that are ineffective, failure to follow up abnormal test results, confusing one patient with another, reliance upon inaccurate or incomplete patient data, intentionally or accidentally subverting Clinical Decision Systems (CDS), automatic discontinuation of a prescription, data aggregation leading to erroneous data reporting, and prolonged EHR downtime among other legal related mandate risks.
What is EHR testing?
Testing the implemented EHR ensures that every system in place is put through its paces to ensure data tables and files are loading properly, data collected are processed and store correctly. In addition, it ensures that the system interfaces work as intended, that the workflows have been adjusted appropriately, that alerts are properly triggered and responding correctly, that the reports are generated accurately and completely and that the security system is also checked to ensure it is correct.
Why is EHR important?
EHR increases the logistic productivity of workflows and offers a safer way to care for patients. To ensure efficiency, there is a series of steps the provider’s staff must follow to ensure proper implementation and handling of the EHR system. Before using the implemented EHR, it is recommended to have a testing protocol in place to ensure areas of possible staff confusion are identified and controlled. Using a proper implementation strategy for a new EHR system can facilitate success, minimize delays, and increase health care worker’s satisfaction and decrease the chances of usability being compromised.
What is the selection and implementation plan?
This article discusses the selection and implementation plan that will primarily consist of assessing existing institutional workflows for each department, and it outlines the necessities and inclinations of the institution to include in the EHR system for the organization to function properly. Resources and tools are included to assist in the selection of the product as well as ideas on how to train staff and evaluate staff readiness. Regulatory requirements are also included for consideration during the initial process.
How long does it take to implement an EHR?
The implementation process will first consist of performing an evaluation of the current organization’ s workflows for every department in two to three days, define the needs and preferences of the organization to have in the EHR for the hospital to function planned into one to three months, including hardware needs, deployment of selection and training of super users, to take about one week, and then plan the implementation and staff education to go live in about one more month. The plan for complete implementation roll out from go-live day to full adoption will be between six and eight months.
What is connectivity with external organizations?
Connectivity with external organizations is accurate and complete as authorized (e.g., portal access to/from hospital/clinic, continu ity of care record to referrals, personal health records for patients, disease management to/from health plan).
What is alerts and clinical decision support?
Alerts and clinical decision support provides appropriate reminders and prompts. Use scripts to test various scenarios.
What is an EHR?
As defined by the Center of Medicare and Medicaid Services (CMS), “an electronic health record (EHR) is an electronic version of a patient’s medical history, that is maintained by the provider over time, and may include all of the key administrative clinical data relevant to that person’s care under a particular provider , including demographics, progress notes, problems, medications, vital signs, past medical history, immunizations, laboratory data and radiology reports [1].” While it is said that electronic health records are the next step in the evolution of healthcare, the cyber-security methodologies associated with the adoption of EHRs should also be thoroughly understood before moving forward [2]. Due to the sensitive nature of the information stored within EHRs, several security safeguards have been introduced through the Health Insurance Portability and Accountability Act (HIPAA) and the Health Information Technology for Economic and Clinical Health (HITECH) Act.
What is the most important barrier to entry when considering the adoption of electronic health records in the healthcare industry?
The privacy of patients and the security of their information is the most imperative barrier to entry when considering the adoption of electronic health records in the healthcare industry. Considering current legal regulations, this review seeks to analyze and discuss prominent security techniques for healthcare organizations seeking to adopt a secure electronic health records system. Additionally, the researchers sought to establish a foundation for further research for security in the healthcare industry. The researchers utilized the Texas State University Library to gain access to three online databases: PubMed (MEDLINE), CINAHL, and ProQuest Nursing and Allied Health Source. These sources were used to conduct searches on literature concerning security of electronic health records containing several inclusion and exclusion criteria. Researchers collected and analyzed 25 journals and reviews discussing security of electronic health records, 20 of which mentioned specific security methods and techniques. The most frequently mentioned security measures and techniques are categorized into three themes: administrative, physical, and technical safeguards. The sensitive nature of the information contained within electronic health records has prompted the need for advanced security techniques that are able to put these worries at ease. It is imperative for security techniques to cover the vast threats that are present across the three pillars of healthcare.
How does cryptography protect health information?
The use of cryptography has also ensured the security of protected health information in electronic health records systems. Specifically, encryption has enhanced security of EHRs during the exchange of health information. The exchange process of health information has a set specification provided by the meaningful use criteria, which requires the exchange process to be recorded by the organizations when the encryptions are being enabled or inhibited [14, 23]. The Health Insurance Portability and Accountability Act (HIPAA) designed a method for the use of cryptography to ensure security [16]. HIPAA expanded its security and privacy standards when the US Department of Health and Human Services (DHHS) created the Final Rule in 2003 [20]. Under the Final Rule, HIPAA expanded the criteria for organizations when creating, receiving, maintaining, or transmitting protected health information (PHI) [20, 29]. One method specifically mentioned is the use of decryption [6]. For example, decryption ensures the security of EHRs when viewed by patients. Digital signatures are the solution to preventing breaches of PHI when patients view personal information. This method has proven to be a preventative measure of security breaches [11, 24]. Encryption and decryption methods are also successful when used to secure PHI accessed through mobile agents. By securing mobile agents for transmission by patients between facilities, electronic health records are not only more secure, but also more accessible [19]. Another form of cryptography is the usage of usernames and passwords. The utilization of usernames and passwords can ultimately prevent security breaches by simply incorporating personal privacy regarding passwords and requiring users to frequently change personal passwords [15, 18, 30]. The password should not include meaningful names or dates to the individual in an attempt to avoid the likelihood that a hacker could speculate the password. The utilization of usernames and passwords are also a useful security technique for providers in establishing role-based access controls. Role-based access controls restrict information to users based on username and password credentials that are assigned by a system administrator. This security technique protects the information within EHRs from internal breaches or threats [28]. It is also important that the employee remembers to log out of the system after each use to avoid leaving protected health information (PHI) visible to unauthorized personnel [15].
What are the security concerns of electronic health records?
Currently, privacy and security concerns over protected health information are the largest barrier to electronic health record adoption; therefore, it is imperative for health organizations to identify techniques to secure electronic health records [23]. After analyzing the results, the researchers concluded that the two most frequently discussed security techniques mentioned throughout the selected sample were the use of firewalls and cryptography. Other notable security techniques such as cloud computing, antivirus software, and chief information security officers (CISOs) were also mentioned throughout the readings but implemented based on budgetary schemes and restrictions. The synopsis of the security techniques mentioned Table Table11highlight several interesting points.
What is HIPAA 3 tier model?
There are many aspects of security for technology, which is the reason for HIPAA’s three-tier model of physical, technical, administrative. There are security techniques that fit each of these categories, but there is no panacea of technique to thwart spurious (or accidental) breaches. Technology security officers are trained by many different organizations such as SANS, Microsoft, and the Computer Technology Industry Association. In November 2016, SANS hosted a Healthcare CyberSecurity Summit and Training seminar in Houston, Texas where it provided an overview of the most pressing security issues in healthcare and how to adopt healthy cyber-hygiene habits in the server room. SANS hosts these specialized seminars regularly because the cybersecurity environment is fluid, and because there is no magic combination of security controls and habits that will repel all boarders from key business data. As a result, there is no measuring tool to assess the success of one tool over another: Instead, security professionals balance their security programs with physical, technical, and administrative security controls along with an ever-present eye on the security landscape to observe breaches experienced by others and enact further controls to mitigate the risk of the same breach occurring in their facilities.
What are the three modalities of HIPAA?
As a group, we decided to analyze each article through the three modalities of security as outlined by HIPAA: Physical, technical, and administrative. We created a column for each of these themes and counted if an article used one or more of them. We also detailed the security techniques mentioned in the article into a summary table.
How many articles were read in the security review?
Through the database queries, 25 articles were identified for inclusion in this review based upon common security themes and techniques. All 25 research articles were read and analyzed by at least two researchers to ensure their relevance to this manuscript and increase the overall validity of this study.
What are the two features that the ONC rule highlights and both give valuable patient access?
Patient portals and mobile health apps are two features that the ONC rule highlights and both give valuable patient access.
How does ONC work?
The ONC can work with health IT developers to enhance health equity by simplifying and optimizing patient portals and mobile apps. Source: Thinkstock.
What is ONC interoperability rule?
The ONC interoperability rule forced new criteria for EHRs to make all patient data available through application programming interfaces (APIs), which will allow providers and patients to have access to health information.
What is the use of modern computing standards and APIs?
“This requires using modern computing standards and APIs that give patients access to their health information and give them the ability to use the tools they want to shop for and coordinate their own care on their smartphones ,” Rucker continued.
What can health IT professionals address?
In an effort to fix these issues, health IT professionals can address technology access, digital health literacy, and inclusive design problems.
Is digital health literacy lacking?
Next, digital health literacy is lacking across the country. Not only can some individuals not access their health information, but most cannot process and understand the digital information.
Should state and local programs expand and increase broadband access?
The writers said state and local programs should expand and increase broadband access. Providers can also help by asking patients about their technology access and how they can adapt once given the answer.
What is the barrier to mobile health apps?
About one-third of polled healthcare organizations stated that they provide “organizational-specific apps” to the patient community. The survey also discovered a major barrier that is standing in the way of leveraging mobile health apps and technologies to boost patient care. This barrier is lack of funding across several facilities.
How many healthcare providers responded to the HIMSS survey?
Nearly 240 healthcare providers responded to the HIMSS survey and illustrated that mobile health apps and technologies are being utilized across the healthcare spectrum to boost patient engagement. For instance, almost 90 percent of survey takers reported using mobile technology to improve patient interest and satisfaction with their establishment.
Popular Posts:
- 1. harborview patient portal
- 2. augusta patient portal
- 3. the nurse has received report regarding her patient in labor. the woman’s last vaginal
- 4. noah clinical laboratory patient portal login
- 5. the orthopedic group patient login
- 6. patient portal for rocky mountain hospital for children
- 7. generate cost report for patient
- 8. https://patientportal.healthtronics.com/patientportal5/practices/500178/patient/login
- 9. niagara family medicine patient portal login
- 10. stonewall jackson patient portal