Two-Step Authentication - UPMC Health Plan
10 hours ago How do I log into two-factor authentication? Activate 2-Step VerificationOpen your Google Account.In the navigation panel, select Security.Under “Signing in to Google,” select 2-Step Verification. Get started.Follow the on-screen steps. How do you keep patient portals secure? >> Go To The Portal
What is two-step authentication and how does it work?
Two-step authentication is a security process that provides additional protection when you sign in to your digital account. You will be asked to set up two-step authentication once. Afterward, you will be asked to complete two-step authentication when you sign in for the first time and periodically after that to verify your identity.
How do I enroll for 2-step authentication for VPN access?
For VPN access to UVA Health System secured network (i.e., offsite access to Epic, PACS, work computer) requires 2-step authentication. Enrolling for 2-step authentication is easy. You will first need to request VPN access via the Online Access Request application (link provided below) You also need the Duo mobile app.
Do I need to enroll for 2-step authentication for duo?
( Note: If you are already enrolled in Duo and using it for VPN or Email there are no additional steps that need to be completed.) For VPN access to UVA Health System secured network (i.e., offsite access to Epic, PACS, work computer) requires 2-step authentication. Enrolling for 2-step authentication is easy.
What is 2-step enrollment and how does it work?
2-step enrollment requires you to register your preferred authentication method through your choice of text, voice, mobile authenticator app (i.e., Google Authenticator), or a hard token, also known as a security token or authorization token.
How do I do 2-step authentication?
Activate 2-Step VerificationOpen your Google Account.In the navigation panel, select Security.Under “Signing in to Google,” select 2-Step Verification. Get started.Follow the on-screen steps.
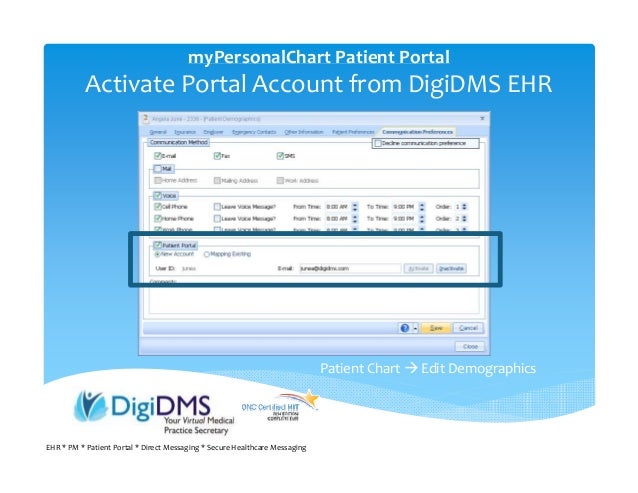
How do I set up Google Authenticator for patient portal?
Set up AuthenticatorOn your Android device, go to your Google Account.At the top, tap the Security tab. If at first you don't get the Security tab, swipe through all tabs until you find it.Under "Signing in to Google," tap 2-Step Verification. ... Under "Authenticator app," tap Set up. ... Follow the on-screen steps.
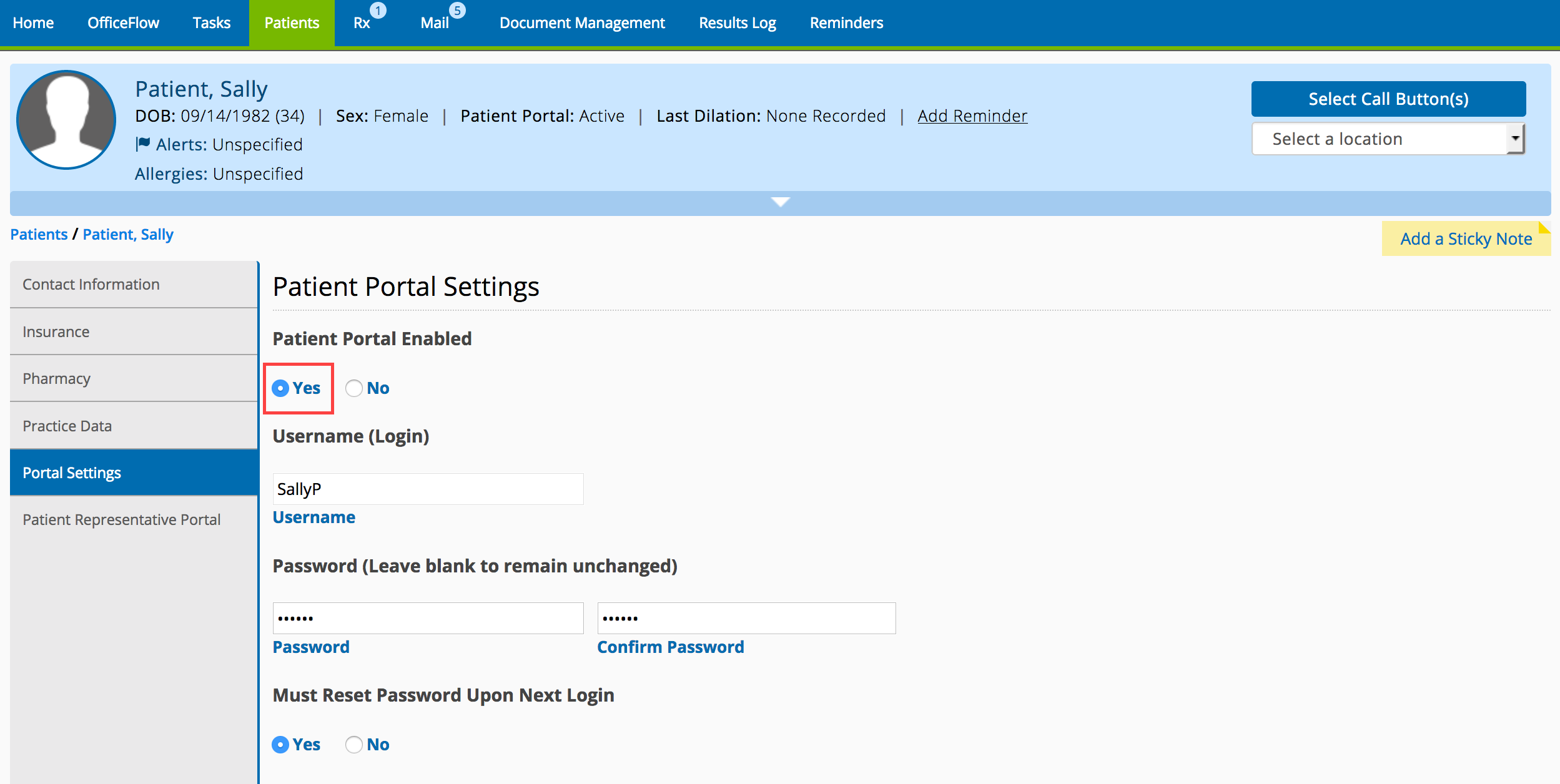
How do you secure a patient portal?
Here are five ways organizations can bring their patient portal security up-to-date and keep their networks safe from unauthorized access:Portal sign-up process should be automated. ... Keep anti-virus and malware software up to date. ... Multifactor verification is a must. ... Protect patient identities with identity solutions.More items...•Mar 20, 2020
Can you bypass the two-factor authentication?
While hackers are able to bypass the two-factor authentication through the bots, they cannot actually hack the account when such verification is enabled. Instead, they will need the authentication code from the targeted user, and if you do not share it with them, your account is sure to be safe from such an intrusion.Nov 11, 2021
How do I use NextGen patient portal?
0:050:58Patient Portal – How to check into your appointment through ... - YouTubeYouTubeStart of suggested clipEnd of suggested clipYou can go ahead and do so on the patient portal and then it will also allow you to provide clinicalMoreYou can go ahead and do so on the patient portal and then it will also allow you to provide clinical. Information as part of the intake. Process. Once complete check-in process is selected.
How can I get verification code without phone?
If you have a smartphone but no Internet access, you can use the Google Authenticator app — which you will need to download ahead of time — to receive codes for Android, BlackBerry or iOS instead of printed codes or phone calls.Dec 17, 2015
What types of patient portals are there?
There are two main types of patient portals: a standalone system and an integrated service. Integrated patient portal software functionality usually comes as a part of an EMR system, an EHR system or practice management software. But at their most basic, they're simply web-based tools.Feb 12, 2021
What is a patient portal quizlet?
Patient Portal. Web-based service that provides patients online access to their health information and allows them to communicate with their healthcare provider, schedule appointments, view billing statements, and accomplish more health-related tasks.
Why do patients not use patient portals?
For some people, they avoid using the portals altogether for reasons like security issues, low health literacy, or lack of internet. Even for those who do access their accounts, there are still other disadvantages of patient portals.Nov 11, 2021
Can hackers bypass two step verification?
Hackers can now bypass two-factor authentication with a new kind of phishing scam. Two-factor authentication, the added security step that requires people enter a code sent to their phone or email, has traditionally worked to keep usernames and passwords safe from phishing attacks.
Can 2-step verification be hacked?
A new study says that 2FAs are not safe and are being hacked with no intervention from the user. The attack is known as "Man-in-the-Middle".Dec 30, 2021
How do I turn off two step verification on Samsung?
Turn off 2-Step VerificationOn your Android phone or tablet, open your device's Settings app Google. Manage your Google Account.At the top, tap Security.Under "Signing in to Google," tap 2-Step Verification. You might need to sign in.Tap Turn off.Confirm by tapping Turn off.
What is the first step of two factor authentication?
The first authentication point in a two-factor process is the password. It should follow the best practices of being unique and users should change the password on a regular schedule. The second step of the two-factor authentication can vary. You should be aware, too, that there is also multi factor authentication (MFA).
What is 2FA authentication?
Two-Factor authentication is a verification process that helps to protect your devices and programs. It’s one of the best practice tips to help keep your data secure and safe from a breach. It’s a step that’s available on a lot of the programs that you use daily. You should also be able to find two-factor authentication options on the devices that you use. Also called 2FA, it’s a process to verify your identity a second time when you access sensitive information or open your device. It also offers a second level of protection, in case your original password is ever compromised. Here, we’ll discuss what it is, why it’s important, how it works, and the options that are available for two-factor authentication with PrognoCIS solutions.
What is 2FA in Verizon?
As the name suggests, 2FA is the process to use a second identification in order to log into an account or access your device. This is an extra measure to secure data, which proves effective. According to the Verizon Data Breach Investigation Report 2019, 80% of hacking breaches were related to passwords.
Is 2FA always MFA?
But multi factor can also use three types of authentication. So, 2FA is always MFA but MFA is not always 2FA. Theoretically, the more authentication used, the safer the data.
Does PrognoCIS have 2FA?
PrognoCIS includes 2FA biometric fingerprint authentication. This fulfills the idea that the second step should be something that no one else can possess. If your password was compromised, a hacker could easily log in without the 2FA feature enabled. With fingerprint authentication, a hacker would not gain access even with your username and password.
Is fingerprint authentication secure?
When the feature is enabled, no one would be able to access your account, even if they had access to your device. Fingerprint authentication is one of the most secure methods you can use to protect your information. The feature is easy to set up and can be enabled or disabled based on your preference.
Can a hacker log in without 2FA?
If your password was compromised, a hacker could easily log in without the 2FA feature enabled. With fingerprint authentication, a hacker would not gain access even with your username and password. Fingerprint authentication is simple to enable and use.
CignaforHCP.com new security feature: Two-step authentication
Cigna is introducing two-step authentication as a security feature for the Cigna for Health Care Professionals website (CignaforHCP.com). This enhancement offers an extra layer of security to help prevent use of the website by unauthorized users, and further protects the privacy of your patients with Cigna-administered coverage.
Overview and frequently asked questions
Cigna is introducing two-step authentication as a security feature for the Cigna for Health Care Professionals website (CignaforHCP.com). This enhancement offers an extra layer of security to help prevent use of the website by unauthorized users, and further protects the privacy of your patients with Cigna-administered coverage.
Popular Posts:
- 1. promoting patient portal
- 2. athena patient portal aslinia
- 3. adime patient report for hypertension
- 4. patient portal vhc
- 5. nursing report sheet one patient per page
- 6. purpose of the patient portal
- 7. manzella family healthcare patient portal
- 8. ut online health patient portal
- 9. johns hopkins white marsh patient portal
- 10. vhs medstreaming net patient portal