Two-Factor Authentication: A No Brainer to Protect …
32 hours ago How do I log into two-factor authentication? Activate 2-Step VerificationOpen your Google Account.In the navigation panel, select Security.Under “Signing in to Google,” select 2-Step Verification. Get started.Follow the on-screen steps. How do you keep patient portals secure? >> Go To The Portal
With two-factor authentication, Healthix can mitigate and reduce risk by sending an authorization request to a user’s mobile device or email, depending on the organization’s policy, to ensure that whomever logs into the patient portal is in fact authorized to do so and is authenticated to view that data.
Full Answer
What is two-factor authentication (2FA) and how does it work?
Two-factor authentication (2FA) is an identity and access management security method that requires two forms of identification to access resources and data. 2FA gives businesses the ability to monitor and help safeguard their most vulnerable information and networks. Businesses use 2FA to help protect their employees’ personal and business assets.
What is multi factor authentication and how does it work?
The card itself is one form of authentication. The PIN you use is your second. Many automobiles use forms of this technology, with keycodes on the door and codes in the key fob. Multi factor authentication is used in a lot of different forms to help protect your possessions from theft.
How do I generate a token to verify my identity?
With a mobile device, you can generate your own codes, or tokens, to provide a unique set of letters/numbers to verify your identity. These codes are sent via SMS and are verified through a website or app. It is important to note that the website or app that you’re identifying yourself through is reliable and safe.
How do I set up Google Authenticator for patient portal?
Set up AuthenticatorOn your Android device, go to your Google Account.At the top, tap the Security tab. If at first you don't get the Security tab, swipe through all tabs until you find it.Under "Signing in to Google," tap 2-Step Verification. ... Under "Authenticator app," tap Set up. ... Follow the on-screen steps.
How do I log into two-factor authentication?
Activate 2-Step VerificationOpen your Google Account.In the navigation panel, select Security.Under “Signing in to Google,” select 2-Step Verification. Get started.Follow the on-screen steps.
How do you keep patient portals secure?
These four tips can help organizations bring their patient portal security up-to-date and keep their networks safe from unauthorized access:Automate the portal sign-up process. ... Leverage multilayer verification. ... Keep anti-virus and malware software up-to-date. ... Promote interoperability standards.Oct 16, 2018
Can you bypass the two-factor authentication?
While hackers are able to bypass the two-factor authentication through the bots, they cannot actually hack the account when such verification is enabled. Instead, they will need the authentication code from the targeted user, and if you do not share it with them, your account is sure to be safe from such an intrusion.Nov 11, 2021
How can I get verification code without phone?
If you have a smartphone but no Internet access, you can use the Google Authenticator app — which you will need to download ahead of time — to receive codes for Android, BlackBerry or iOS instead of printed codes or phone calls. Personal Tech invites questions about computer-based technology to techtip@nytimes.com.Dec 17, 2015
How do I get the 6 digit code from Authenticator app?
To receive a one-time-passcode on your cellphone via text message, click Send Code Check your cellphone. You should have received a text message like the image below with a 6-digit verification code: Enter the 6-digit code received via text message on the Extranet login site Click Verify Code.
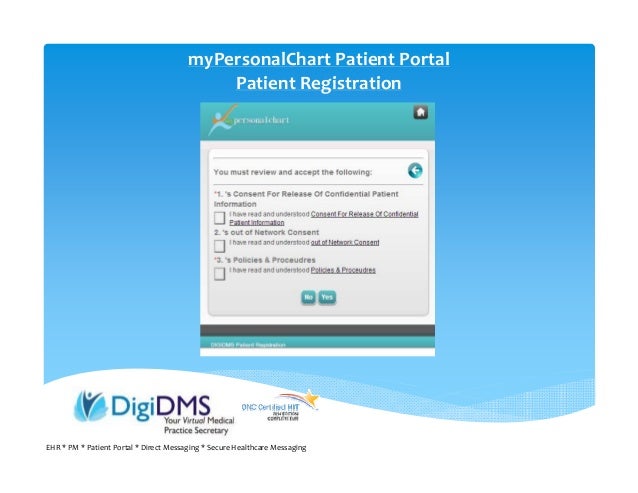
How do you use a patient portal?
If your provider offers a patient portal, you will need a computer and internet connection to use it. Follow the instructions to register for an account. Once you are in your patient portal, you can click the links to perform basic tasks. You can also communicate with your provider's office in the message center.Aug 13, 2020
What are the security issues associated with engaging patients through an online patient portal?
Some of these risks include: reliance on the patient portal as a sole method of patient communication; patient transmission of urgent/emergent messages via the portal; the posting of critical diagnostic results prior to provider discussions with patients; and possible security breaches resulting in HIPAA violations.Mar 1, 2021
What is the advantage of a patient portal for the patient?
Background. Engaging patients in the delivery of health care has the potential to improve health outcomes and patient satisfaction. Patient portals may enhance patient engagement by enabling patients to access their electronic medical records (EMRs) and facilitating secure patient-provider communication.
Can hackers bypass two step verification?
Hackers can now bypass two-factor authentication with a new kind of phishing scam. Two-factor authentication, the added security step that requires people enter a code sent to their phone or email, has traditionally worked to keep usernames and passwords safe from phishing attacks.
How do I get past 2FA discord?
0:545:40How to recover your Discord account with lost Authenticator / Backup codeYouTubeStart of suggested clipEnd of suggested clipIf you are still logged in you can easily access your 2fa backup codes from your account settings.MoreIf you are still logged in you can easily access your 2fa backup codes from your account settings. Using your current password. So at this point you can either use the codes to bypass the 2fa.
How do I bypass Samsung 2-step verification?
To help keep your personal info safe and secure, Samsung now requires two-step verification for all accounts. Two-step verification can no longer be turned off.
What is the first step of two factor authentication?
The first authentication point in a two-factor process is the password. It should follow the best practices of being unique and users should change the password on a regular schedule. The second step of the two-factor authentication can vary. You should be aware, too, that there is also multi factor authentication (MFA).
What is 2FA authentication?
Two-Factor authentication is a verification process that helps to protect your devices and programs. It’s one of the best practice tips to help keep your data secure and safe from a breach. It’s a step that’s available on a lot of the programs that you use daily. You should also be able to find two-factor authentication options on the devices that you use. Also called 2FA, it’s a process to verify your identity a second time when you access sensitive information or open your device. It also offers a second level of protection, in case your original password is ever compromised. Here, we’ll discuss what it is, why it’s important, how it works, and the options that are available for two-factor authentication with PrognoCIS solutions.
How does the fingerprint app work?
Once the password is accepted, the app directs you to a screen to scan your fingerprint. From there, your unique fingerprint is saved as a secondary authentication method. After fingerprint authentication is enabled, a confirmation email is sent to the account on record and the option is added to your login screen.
What is 2FA in Verizon?
As the name suggests, 2FA is the process to use a second identification in order to log into an account or access your device. This is an extra measure to secure data, which proves effective. According to the Verizon Data Breach Investigation Report 2019, 80% of hacking breaches were related to passwords.
How many digits are in a one time password?
The one-time password can be a 4, 5, or 6 digit code. The default in PrognoCIS is to use a 6 digit code, but this can be changed. As we move forward, multi factor authentication will continue to evolve and remain an important part of keeping your data safe.
Is 2FA always MFA?
But multi factor can also use three types of authentication. So, 2FA is always MFA but MFA is not always 2FA. Theoretically, the more authentication used, the safer the data.
Does PrognoCIS have 2FA?
PrognoCIS includes 2FA biometric fingerprint authentication. This fulfills the idea that the second step should be something that no one else can possess. If your password was compromised, a hacker could easily log in without the 2FA feature enabled. With fingerprint authentication, a hacker would not gain access even with your username and password.
